Applies to: VisualSVN Server 5.2 and later
Password guessing attack protection is a countermeasure against attackers who attempt to discover users' login/authentication credentials for VisualSVN Server by systematically trying out a large number of different username and password combinations. Such attacks make lots of repeated login attempts to the server over the network and are usually automated. Depending on the exact technique, they are also known as brute-force or dictionary attacks.
Depending on the authentication mode that you have selected in VisualSVN Server, the valid credentials that an attacker can potentially discover this way are either the dedicated Subversion user credentials (in the Subversion authentication mode) or the regular Windows user account credentials (in the Windows authentication mode with enabled Basic authentication). In the latter case, the Windows user accounts can be both Active Directory accounts and the server computer's local accounts.
Overview of password guessing attack protection in VisualSVN Server
If this protection is enabled in the settings, VisualSVN Server behaves as follows to detect and counteract such potential attacks: if within a short period of time the server receives too many authentication requests with invalid login credentials from any particular IP address, the server temporarily blocks all further requests from this offending IP address. For more information, see Further details on the blocking of offending IP addresses below.
You can enable or disable this protection and can also configure the threshold for the number of failed login attempts, the time window after which the failed login attempt counter is reset and the duration of the blocking of offending IP addresses, so as to hinder attacks while allowing for occasional mistakes by legitimate users. For details, see Settings for password guessing attack protection below.
Availability of password guessing attack protection
The password guessing attack protection functionality is available in both the Subversion authentication mode and the Windows authentication mode in VisualSVN Server. However, in the Windows authentication mode this protection is relevant only if Basic authentication is enabled and is used to log in. This is because if a user logs in to the repository server by means of the Integrated Windows Authentication, this user has necessarily already entered valid credentials when they logged in to their computer.
Enabling password guessing attack protection through VisualSVN Server Manager
To enable password guessing attack protection for VisualSVN Server, follow these steps:
- Start the VisualSVN Server Manager console.
- In the left-hand pane, select the topmost VisualSVN Server node.
- In the top menu bar, click Action | Properties.
- Click the Authentication tab.
- To enable the protection, in the section called Password guessing attack protection, select the Block IP addresses after multiple authentication failures checkbox. Optionally, click the adjacent Advanced button to fine-tune the protection settings. See Settings for password guessing attack protection below for details.
- Click Apply for the changes to take effect.
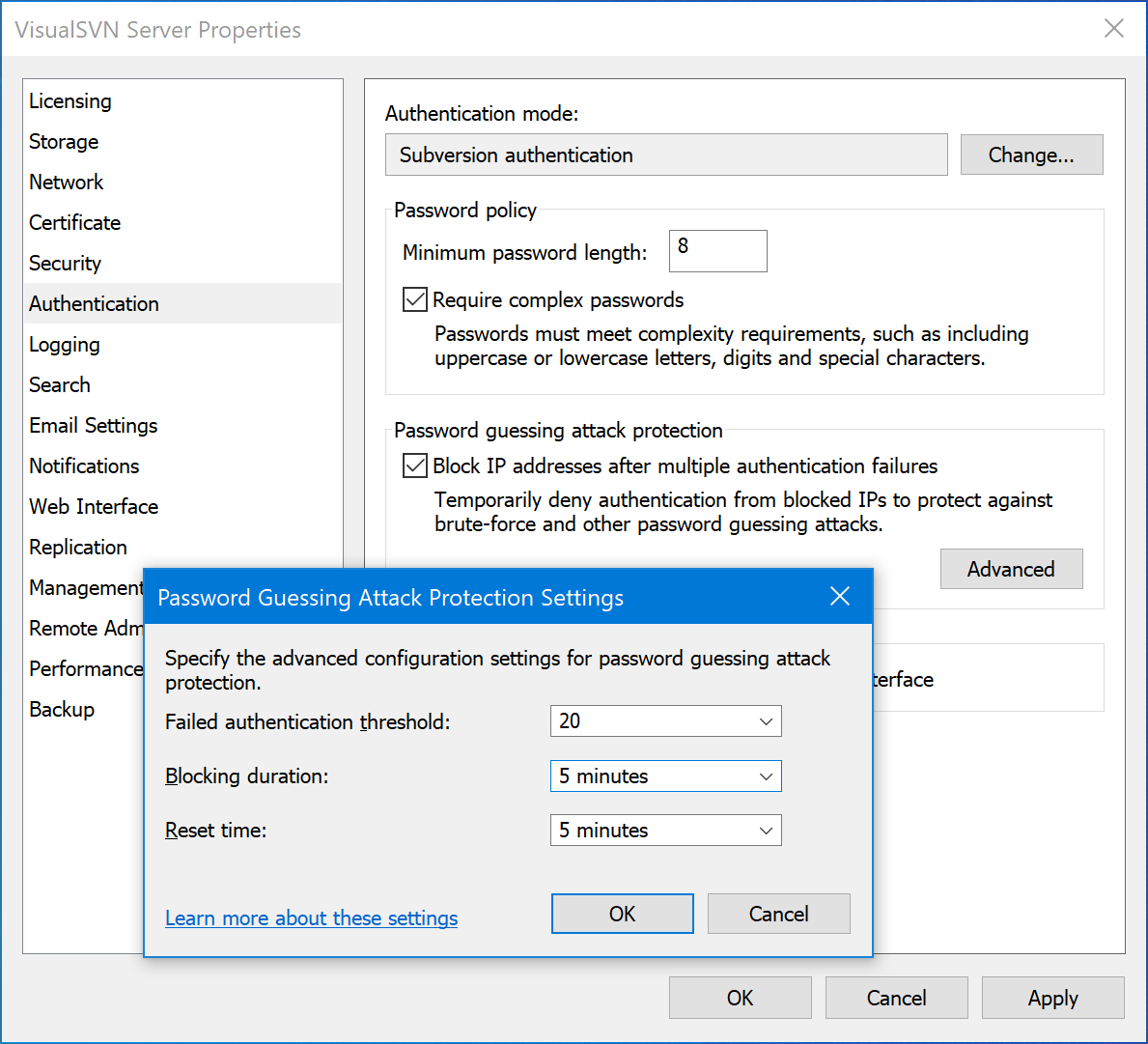
Settings for password guessing attack protection
The password guessing attack protection is controlled by several settings described below. You can find them in the VisualSVN Server Manager console as described in the previous section of this article.
Block IP addresses after multiple authentication failures checkbox - selecting this checkbox enables the protection against password guessing attacks. This is the main setting for this protection functionality.
Advanced settings
The Advanced button in the Password guessing attack protection section is available only when the protection is enabled through the main setting described above.
Failed authentication threshold - sets the threshold value for the counters of failed login attempts. If more than this number of failed login attempts come from a particular source IP address, the server starts to temporarily block any further requests coming from this IP address. The default value is 20 attempts. Note that the failed login attempt counter for each IP address periodically auto-resets to 0, based on the Reset time setting described below.
Blocking duration - sets for how long the offending IP addresses are blocked, before they are again allowed to make any requests to the server. The default value is 5 minutes.
Reset time - sets the amount of time that must elapse since the last failed login attempt from a particular IP address, before the counter of failed login attempts for this IP address is reset to 0. The default value is 5 minutes.
Enabling Password guessing attack protection with PowerShell
Alternatively, you can change or view the settings for the password guessing attack protection by running PowerShell cmdlets on the server, as described below.
Viewing protection settings with PowerShell
To view the current settings of the password guessing attack protection, display the configuration of VisualSVN Server with the Get-SvnServerConfiguration. And, in this configuration, look at the values of the following properties:
-
PasswordGuessingProtection, which corresponds to the main Block IP addresses after multiple authentication failures setting described above in the Settings for password guessing attack protection section. -
PasswordGuessingProtectionBanThreshold, which corresponds to the Failed authentication threshold setting described above. -
PasswordGuessingProtectionBanTime, which corresponds to the Blocking duration setting. -
PasswordGuessingProtectionResetTime, which corresponds to the Reset time setting.
For example, you can display just these properties from the server's configuration with the following command:
Get-SvnServerConfiguration | Format-List PasswordGuessingProtection, PasswordGuessingProtectionBanThreshold, PasswordGuessingProtectionBanTime, PasswordGuessingProtectionResetTime
Changing protection settings with PowerShell
To modify the settings of the password guessing attack protection, use the Set-SvnServerConfiguration cmdlet, specifying one or more of the protection-related configuration properties as parameters (each starting with a hyphen) followed by their desired values. Make sure to provide correct types of parameter values as follows:
-
PasswordGuessingProtectionaccepts named constantsEnabledandDisabledas its possible values. -
PasswordGuessingProtectionBanThresholdaccepts any positive integer value. -
PasswordGuessingProtectionBanTimeandPasswordGuessingProtectionResetTimeeach accept an object of typeTimeSpan, and round its value to seconds.
For example, the following command modifies all the protection settings:
Set-SvnServerConfiguration -PasswordGuessingProtection Enabled -PasswordGuessingProtectionBanThreshold 10 -PasswordGuessingProtectionBanTime (New-TimeSpan -Minutes 4) -PasswordGuessingProtectionResetTime (New-TimeSpan -Minutes 4)
Further details on the blocking of offending IP addresses
What happens when the IP address of a client is blocked
During the time while a client's IP address is blocked (the Blocking duration), the server always replies with an error message to any requests it receives from the blocked source IP address.
When VisualSVN Server blocks a request from a dedicated SVN client application (such as TortoiseSVN or the command-line SVN client) due to this protection against password guessing, the SVN client will receive and display the following error message:
Where the /svn/MyRepository path will differ based on the name of your repository.
In a web browser, when a user attempts to access the server's repository web interface from a blocked IP address, the browser will display a page with the following error message:
Logging blocked IP addresses
The server logs an event when it starts blocking an offending client's IP address or subnet. The events are recorded into the VisualSVN Server event log at the Error log level. They specify the blocked client's IP address and look like this:
After that, for the duration of the blocking, requests from this particular offending IP address/subnet are ignored silently, without causing further event log entries.
Difference in the blocking of IPv4 and IPv6 addresses
When the offending source IP address (that sends too many invalid
credentials) is an IPv4 address, VisualSVN Server temporarily blocks
requests from this specific IP address. For example, if the offending IP
address is 192.168.1.68, only requests coming from
192.168.1.68 get blocked.
If the offending source IP address is an IPv6 address, then VisualSVN
Server temporarily blocks requests from the entire /64 subnet that the
offending IPv6 address belongs to. That is, it blocks requests from all
those IPv6 addresses in which the first 64 bits (the first 4 out of 8
colon-separated hexadecimal numbers) match the offending IPv6 address.
For example, if the offending IP address is
fd12:3456:789a:000a:0000:0000:0000:0001, the server will temporarily block
access for all addresses in the range from
fd12:3456:789a:000a:0000:0000:0000:0000 up to
fd12:3456:789a:000a:ffff:ffff:ffff:ffff, inclusive.
This is because blocking an individual offending IPv6 address does not provide enough protection, since public IPv6 subnetworks and private local networks using IPv6 normally contain vastly more possible unique IPv6 addresses compared to IPv4 ones, thereby allowing an attack to use a much larger number of unique source IP addresses.
See also
KB179: Understanding the password policy for Subversion authentication
KB165: Using VisualSVN Server PowerShell module